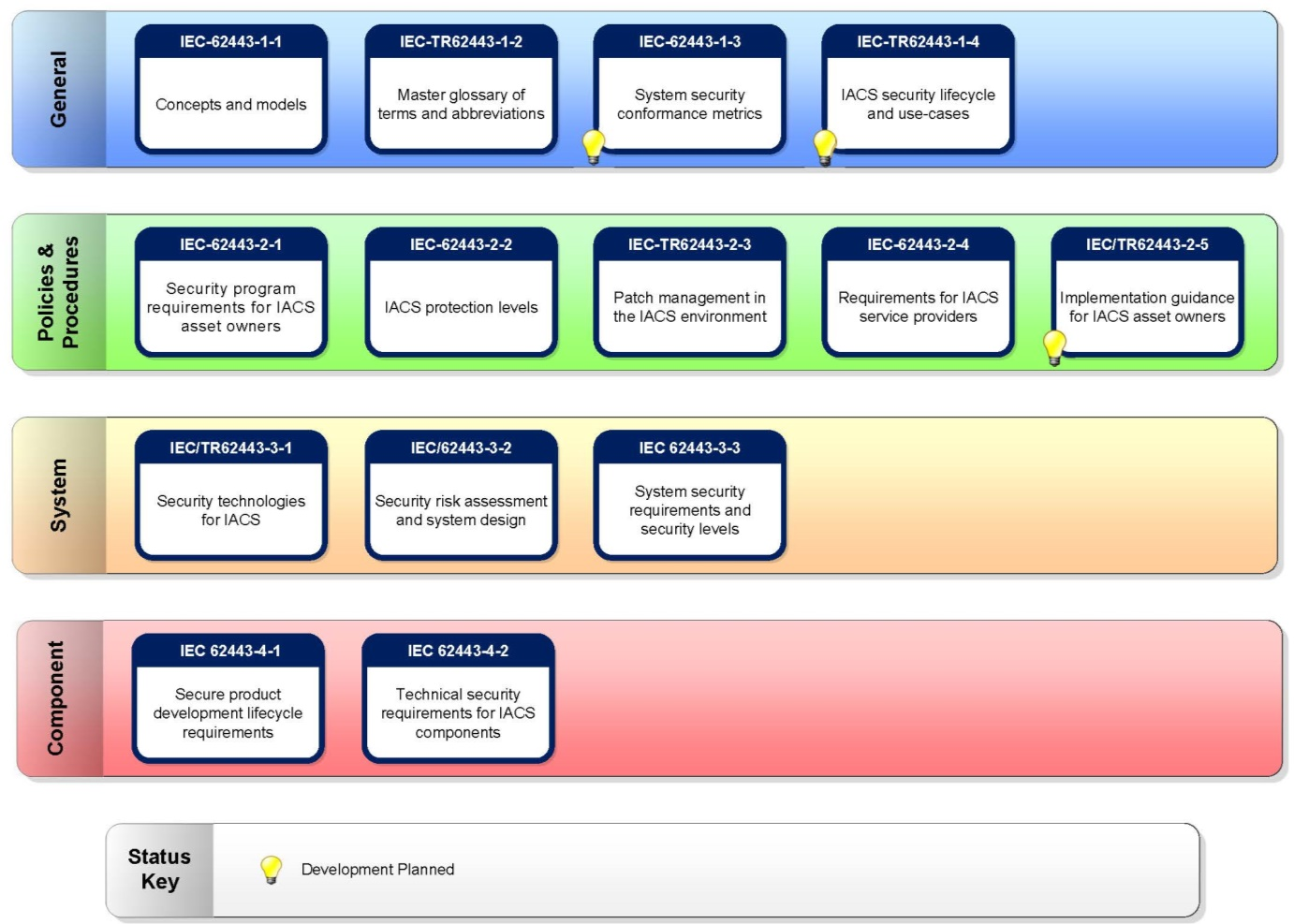
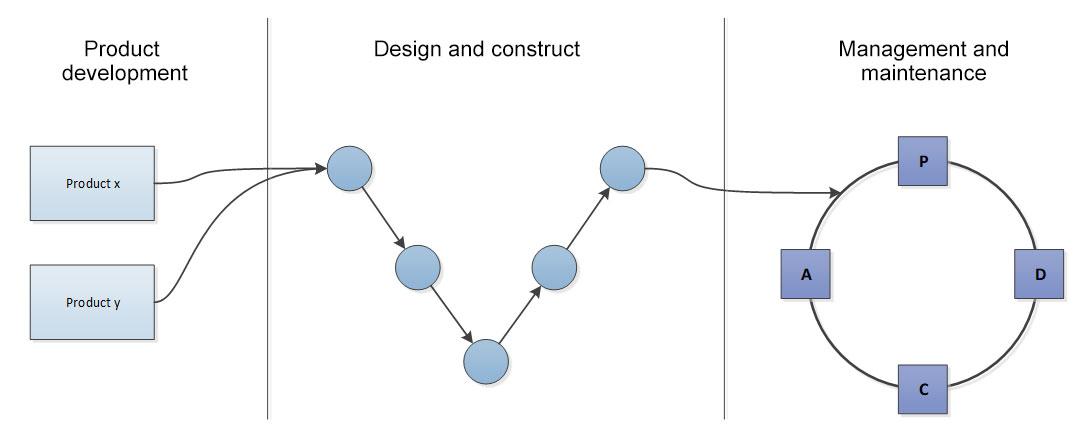
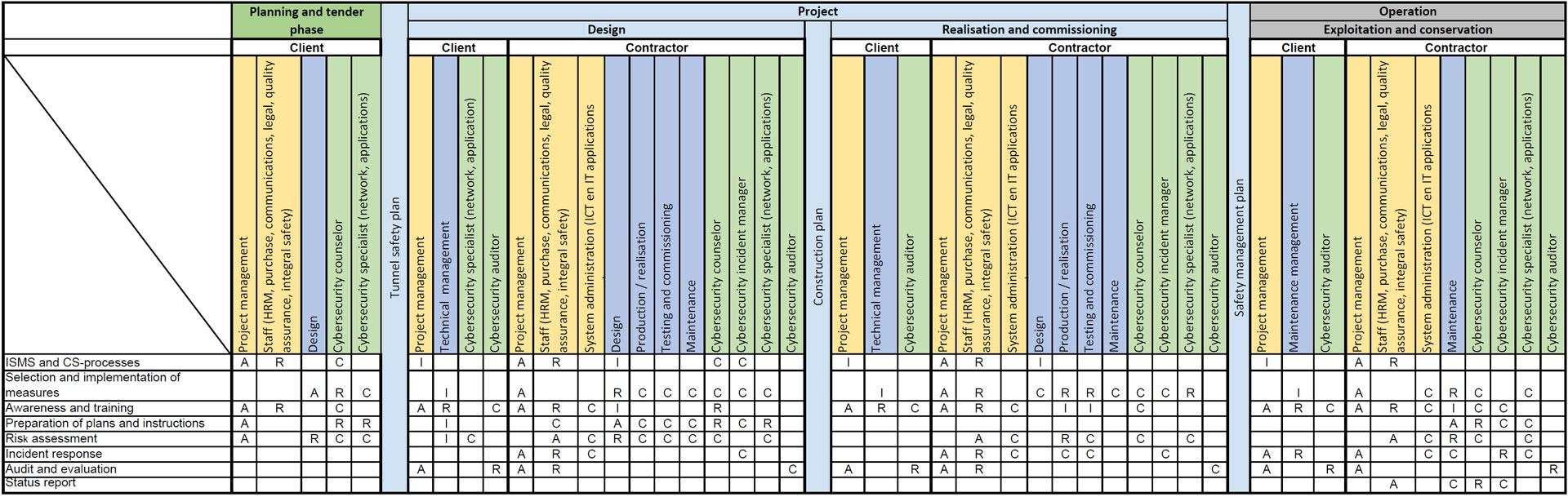
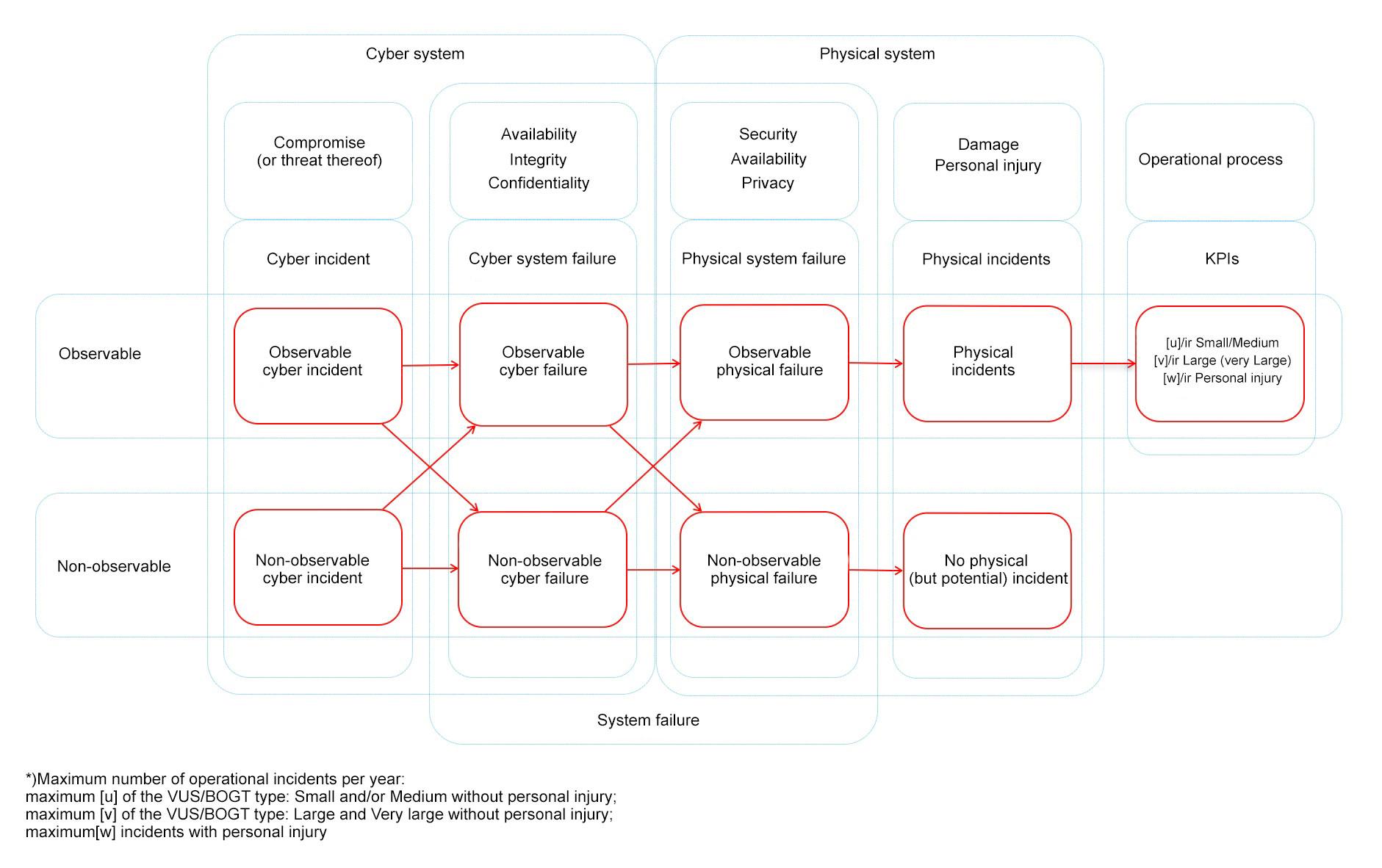
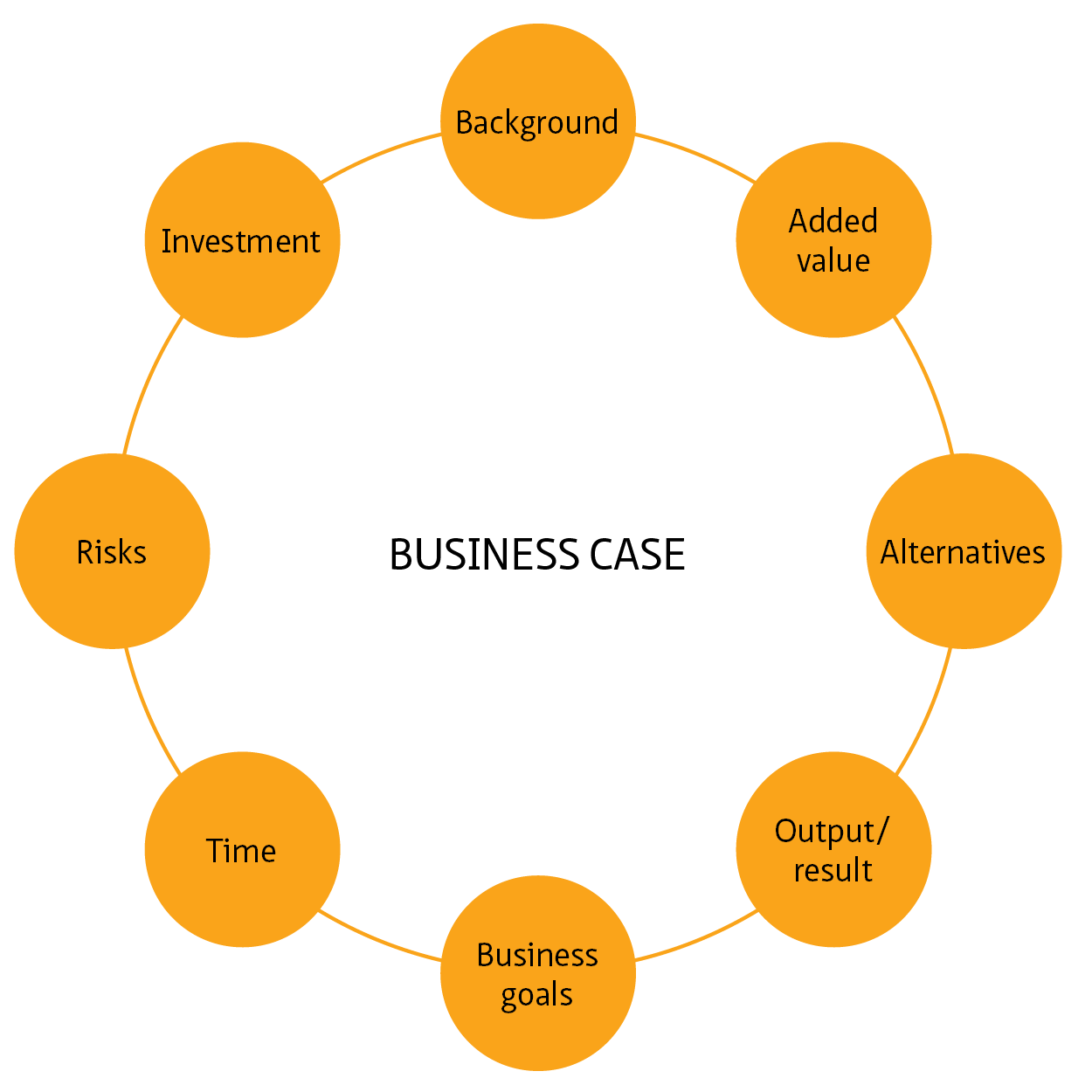
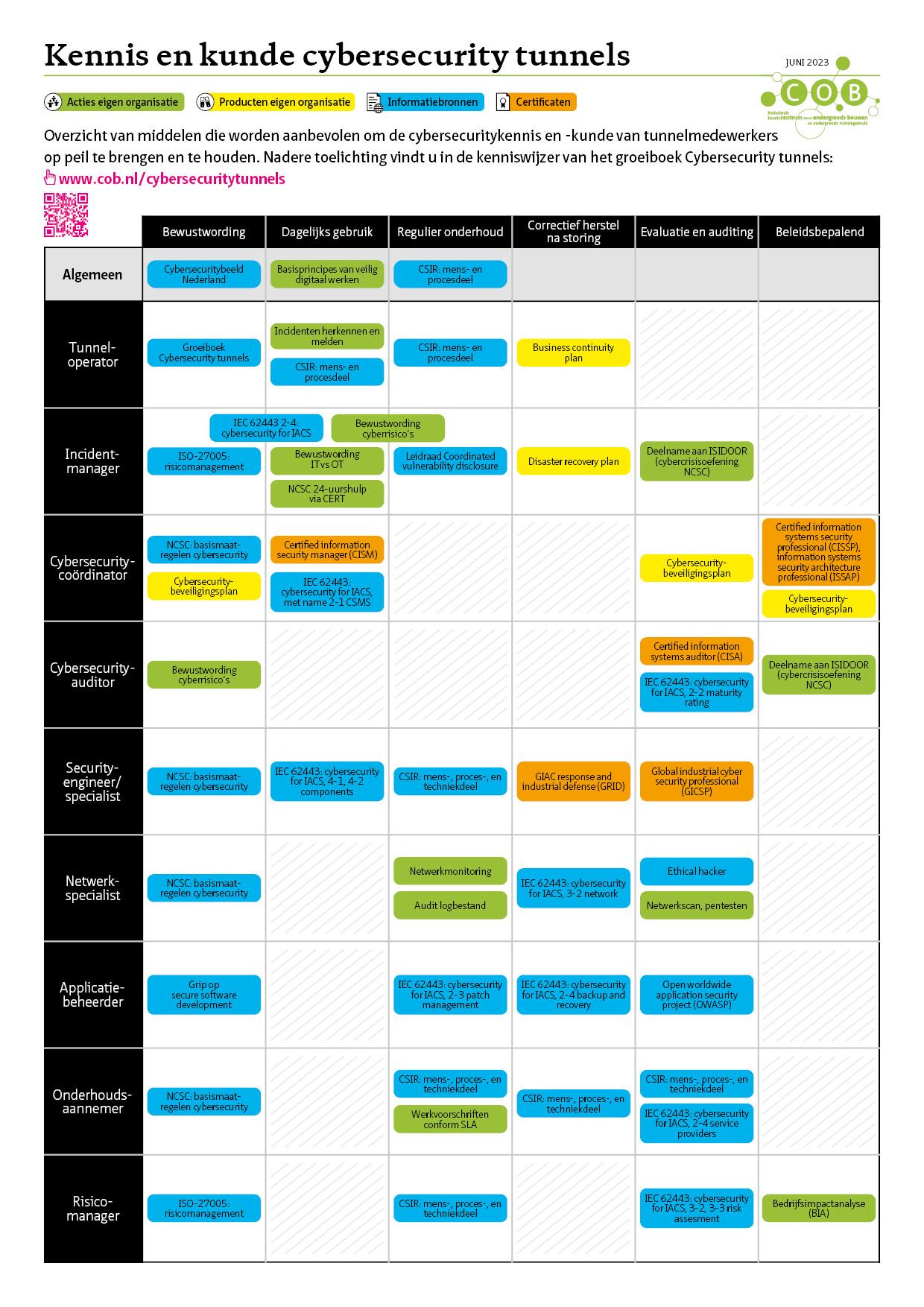
6.5 Drafting a risk analysis [link id=”z89x3″]
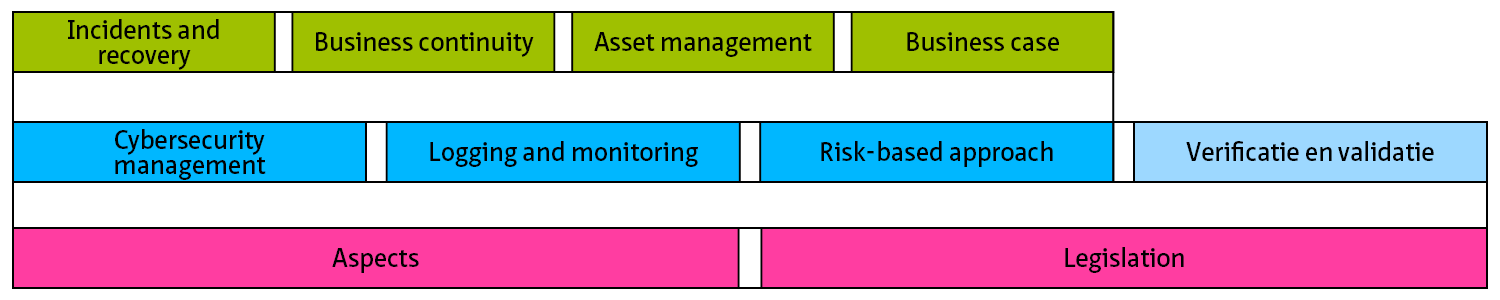
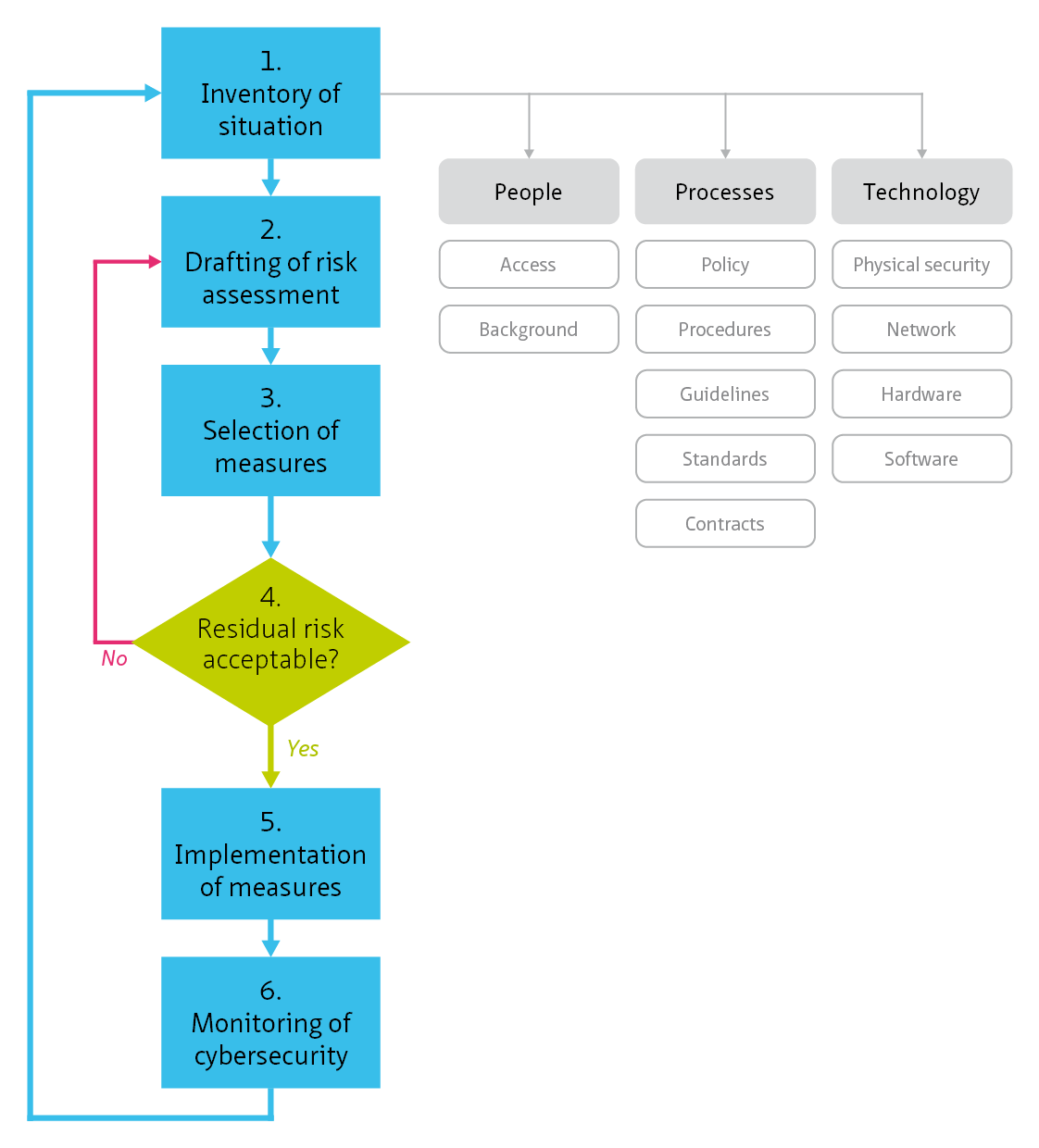
The inventory is followed by the drafting of a risk analysis on the basis of the list of threats presented in the inventory. The threats must be specified as precisely as possible. The classification of aspects 2 The aspects of cybersecurity can help in preparing this list.
The risk can be quantified by determining the probability of occurrence of each threat, and determining the impact, if the threat actually occurs. The risk is then the combination of impact and probability: risk = probability x impact.
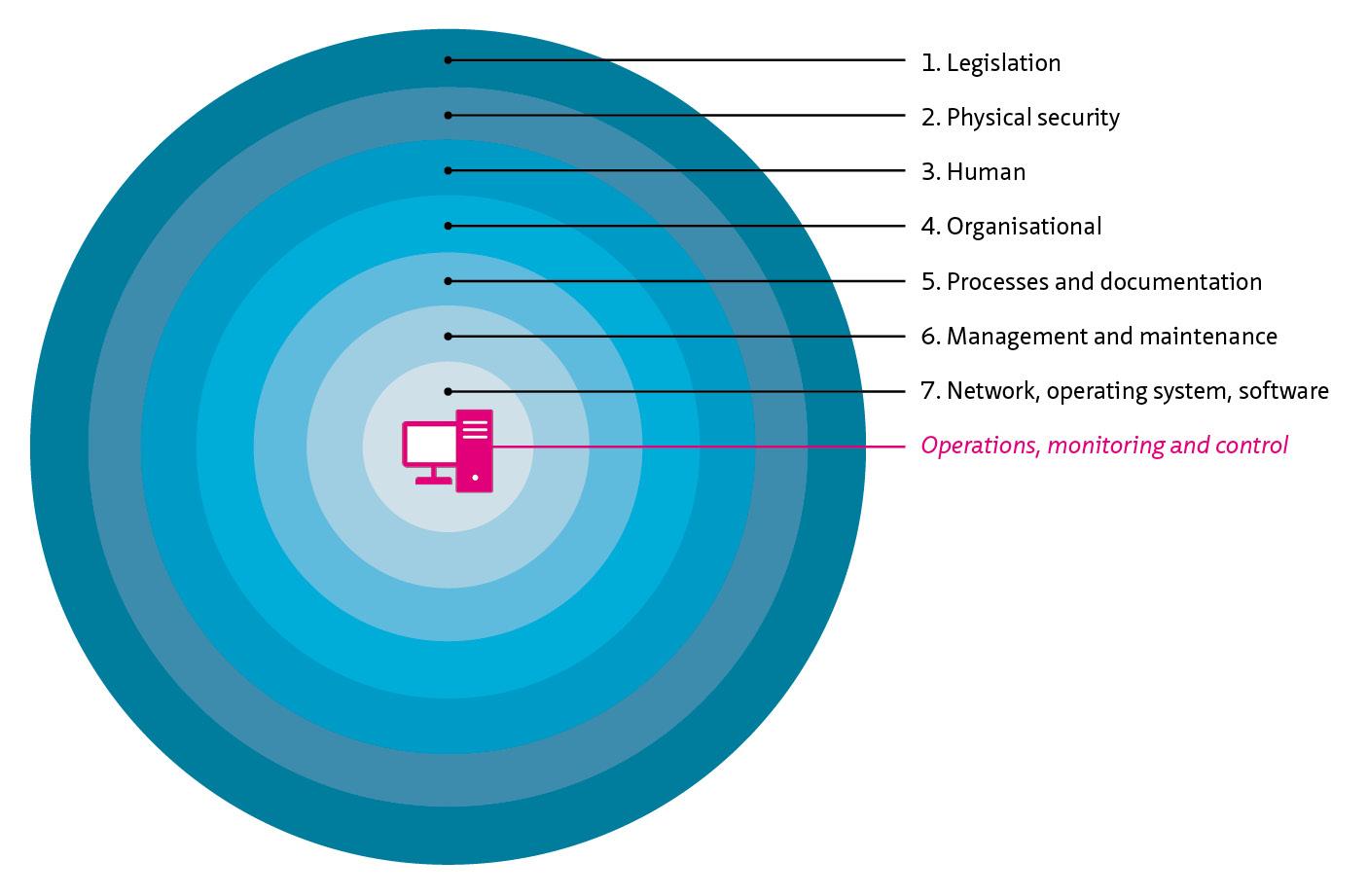
Risk assessment by Rijkswaterstaat
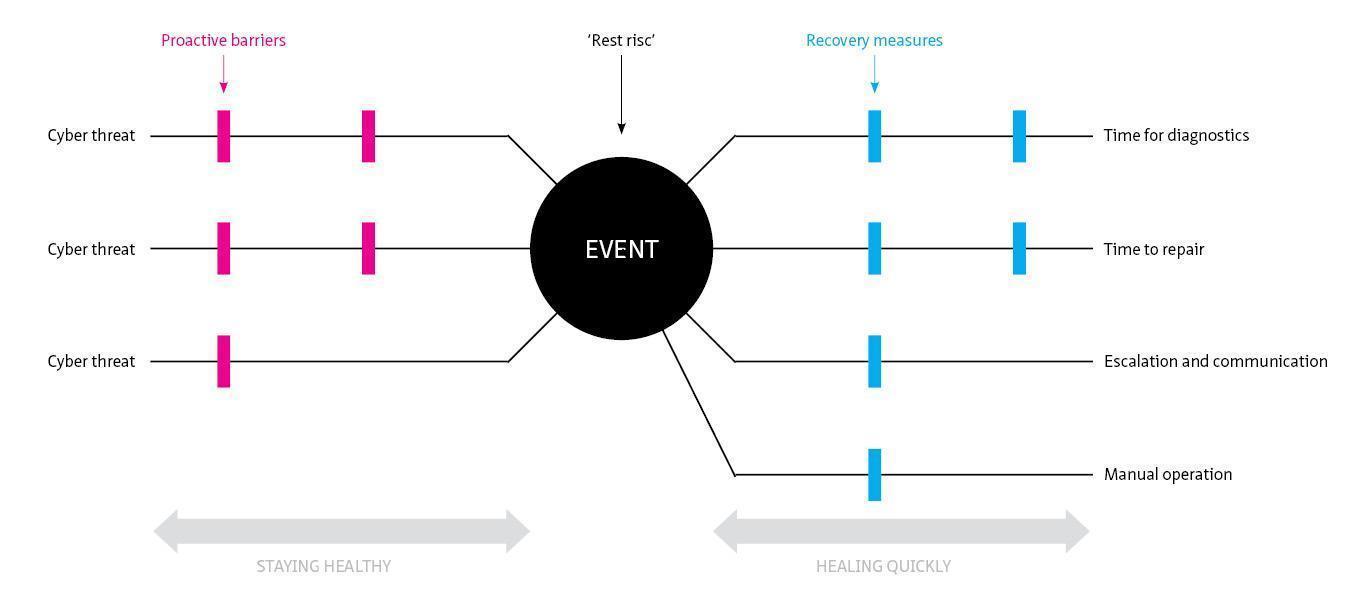
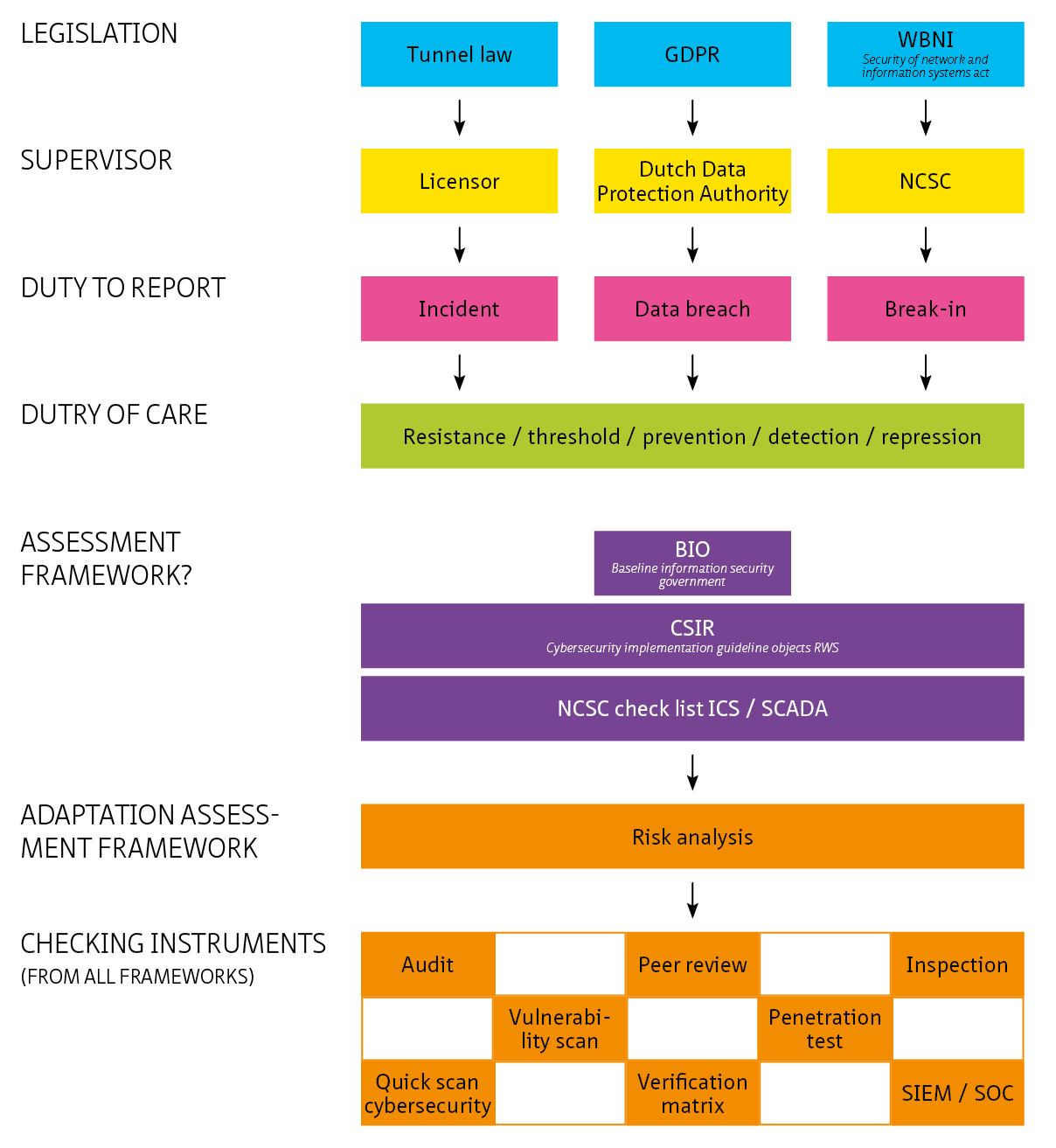
Rijkswaterstaat uses the formula ‘risk = threat x vulnerability x impact’ to determine the risk to cybersecurity. See the diagram below (Source: presentation on cybersecurity for ISAC by Turabi Yildirim, Rijkswaterstaat).
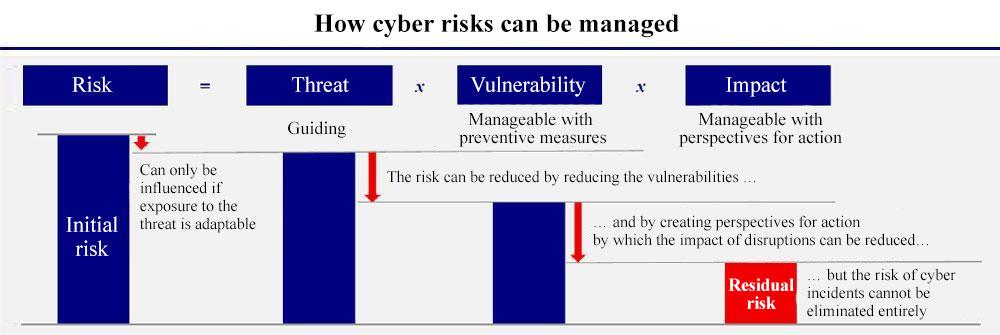
Figure 6.3: Risk assessment at Rijkswaterstaat
A ‘cybersecurity incident log’ is a tool for monitoring the security assessment for a specific operational environment or system. Cybersecurity assessments are generally drawn up by cybersecurity experts. However, it is advisable to have the realism of these assessments peer-reviewed, and to have the client and the users evaluate their impact on the operation, especially with respect to the acceptance of residual risks (see below) since they have an impact on the operation.
Methods
Broadly speaking there are two methods for drafting a risk analysis:
-
-
- Qualitative: qualitative estimates of the risks are made.
- Quantitative: the risks are quantified in measurable criteria, usually expressed in terms of financial consequences or the number of acceptable incidents (residual risk) or cases of personal injury.
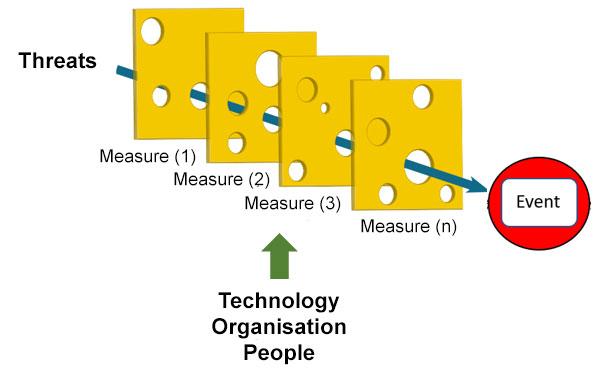
In the case of industrial automation, use is often made of a fault tree analysis or a failure mode, effects (and criticality) analysis, de FME(C)A. Specifically for cybersecurity, a threat model can be drafted.
Sources for risk analysis and management for cybersecurity are:
-
-
OT systems are subject to the IEC 62443-3-2 standard. This standard describes the security risk assessment and system design.
-
-
- ISO 27000: This series comprises a variety of information security sources. The ISO 27000 standard is aimed primarily at IT environments such as office automation (SAP, Microsoft Office, etc.). For certain aspects, it is not suitable for OT systems such as operation, management and monitoring of tunnels (see also Appendix 2 OT vs IT). After all, in the case of tunnels, continuous use is essential, which is not the case for office automation.
- ISO 31000, risk management
- Guides and guidelines ProRail and Rijkswaterstaat
Not separate domains
Whereas IT and OT have traditionally been separate domains, nowadays a growing number of manufacturing processes depend on IT solutions. As a result, the OT environment is affected by malware from the IT environment more frequently. In practice, more than half of the malware problems in an OT environment arise from the organisation’s own IT systems. Moreover, the development of the Internet of Things (IoT) has now reached the OT world. Naturally, this creates many new possibilities, but unfortunately also new security threats; an increase in the number of factory sensors within a factory or an object represents a larger ‘attack surface’. Specific knowledge and expertise, as well as a clear understanding of the impact of a cyber attack and how to defend against it, are needed to reconcile cybersecurity in the two domains.
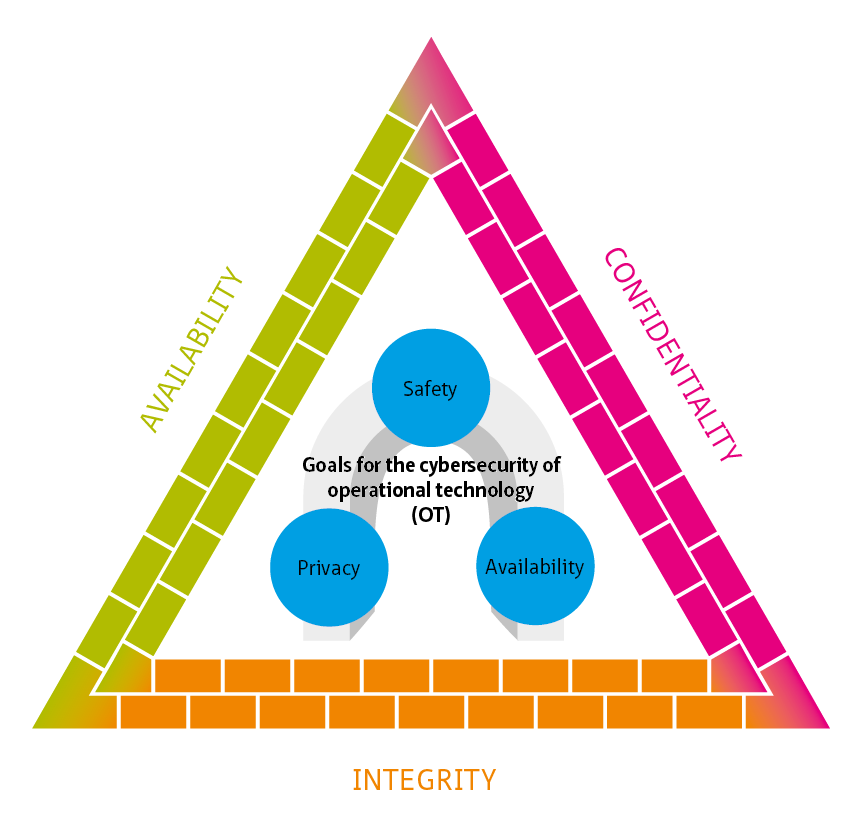
Availability and integrity are top priorities on the OT agenda. Cyber defences have to protect them, but at the same time must not disrupt the business processes. Equally, threats to the IT environment must be prevented (mitigated) while the priority might be to preserve confidentiality for example. An obvious solution for properly securing both domains is an integrated ‘IT/OT’ approach to cybersecurity. A specific threat assessment must be drawn up for every operation and for every system. This applies both to the design process and in determining (and evaluating) the specific cybersecurity measures.
Operation
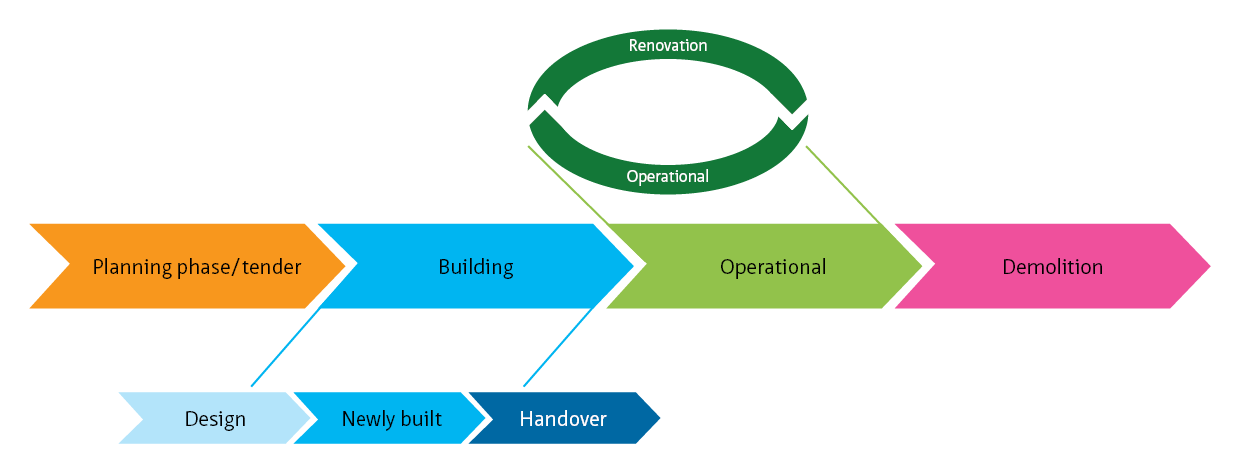
Operation encompasses day-to-day tasks for the operational tasks (normal and in an emergency) and for maintenance and management activities. (maintenance operation).
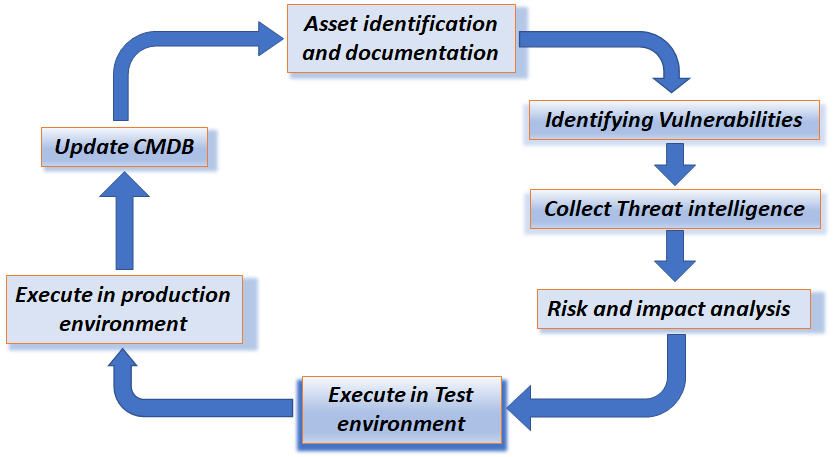
Identifying vulnerabilities and adverse consequences
On the basis of the previously mentioned set of threats, it is possible to define a set of hazards by identifying one or more vulnerabilities and one or more (adverse) consequences, for example by following the step-by-step plan outlined below:
-
-
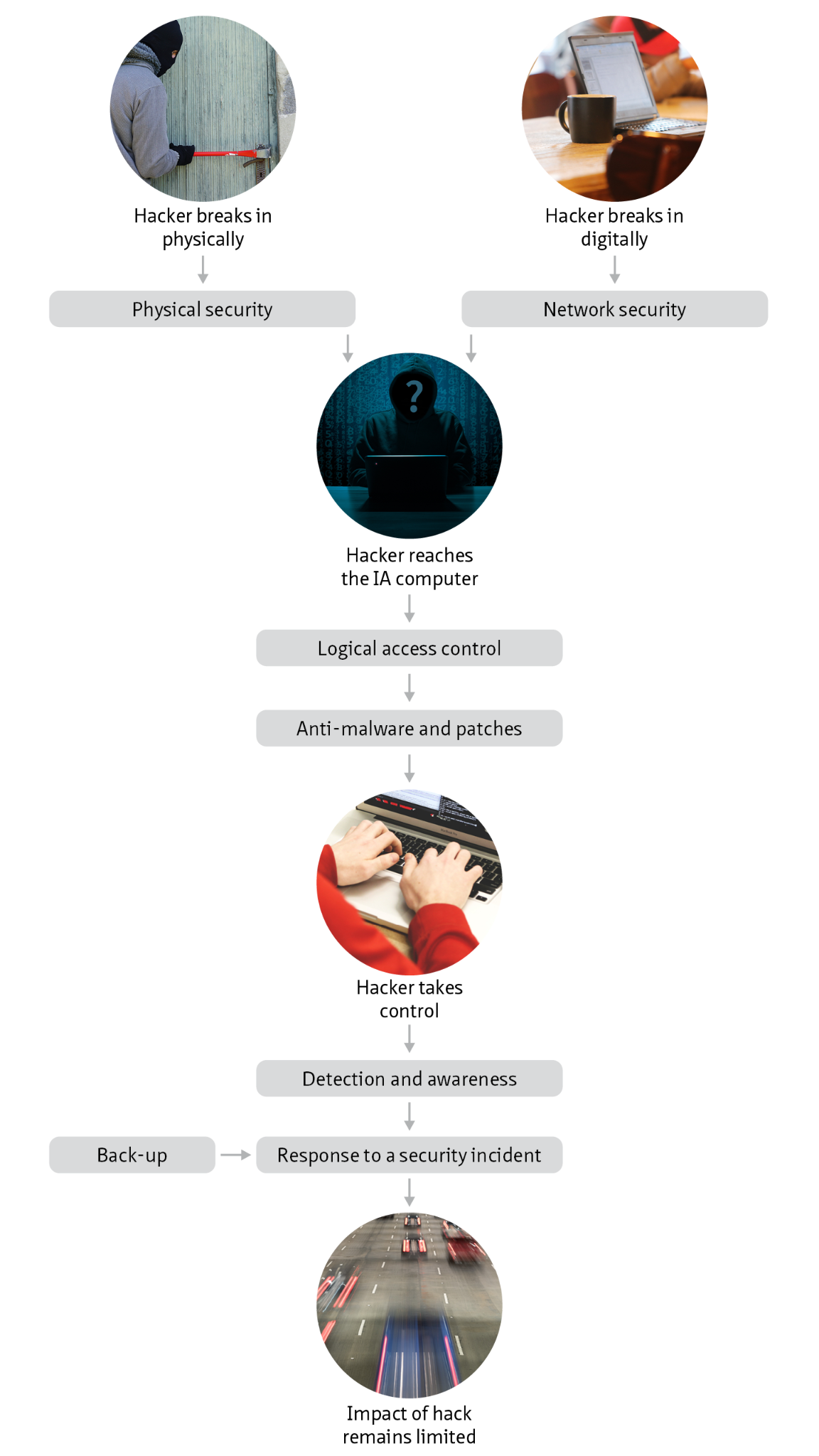
- One of the threats is that unauthorised persons gain access to a technical area.
- The person who drafts the risk analysis must then ask himself what could go wrong if such a situation arises:
- The unauthorised person could deactivate equipment.
- The unauthorised person could gain access to the network.
- The unauthorised person could gain access to a SCADA computer.
- A consequence can be identified for each of these vulnerabilities.
- If equipment is deactivated, the object (the tunnel) can no longer be operated or monitored.
- If someone gains access to a network, they can listen into and manipulate the network traffic, thereby influencing the control system.
- If a person gains access to a SCADA computer, they can operate and control that part of the systems without being able to observe what happens in the tunnel.
- The final consequence can then also be determined:
- If the tunnel cannot be operated, it is no longer safe and has to be closed.
- If the commands transmitted via the network are manipulated, unintended effects can occur in and around the tunnel that have a negative impact on the safety of road users.
- If a person operates a sub installation without understanding the effect of their actions, unintended effects can take place in and around the tunnel that negatively impact the safety of road users.
- Finally, once the complete picture of the threat, vulnerabilities and consequences has been identified, it is possible to estimate the probability of this threat occurring.
- For each of the risks, the risk level is defined and a determination can be made whether this level is or is not acceptable.
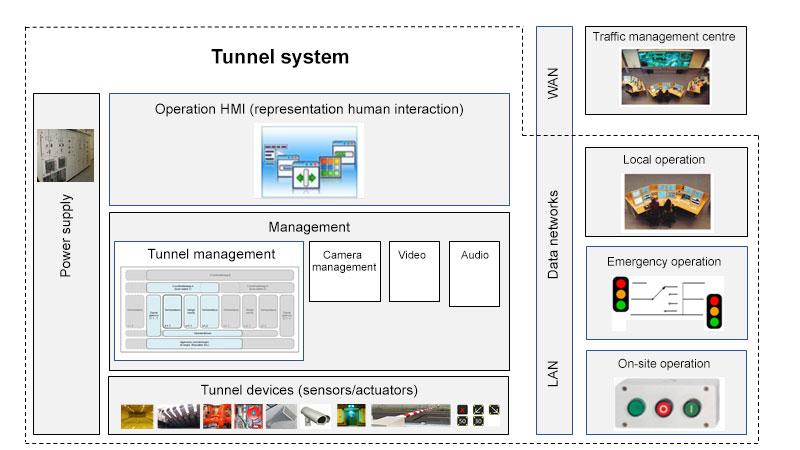
Note: the above summary is intended to be an example of situations that may arise, rather than an exhaustive list. The step-by-step plan outlined above can also be applied to the entire tunnel system but also to sub systems in order to obtain a more detailed picture.
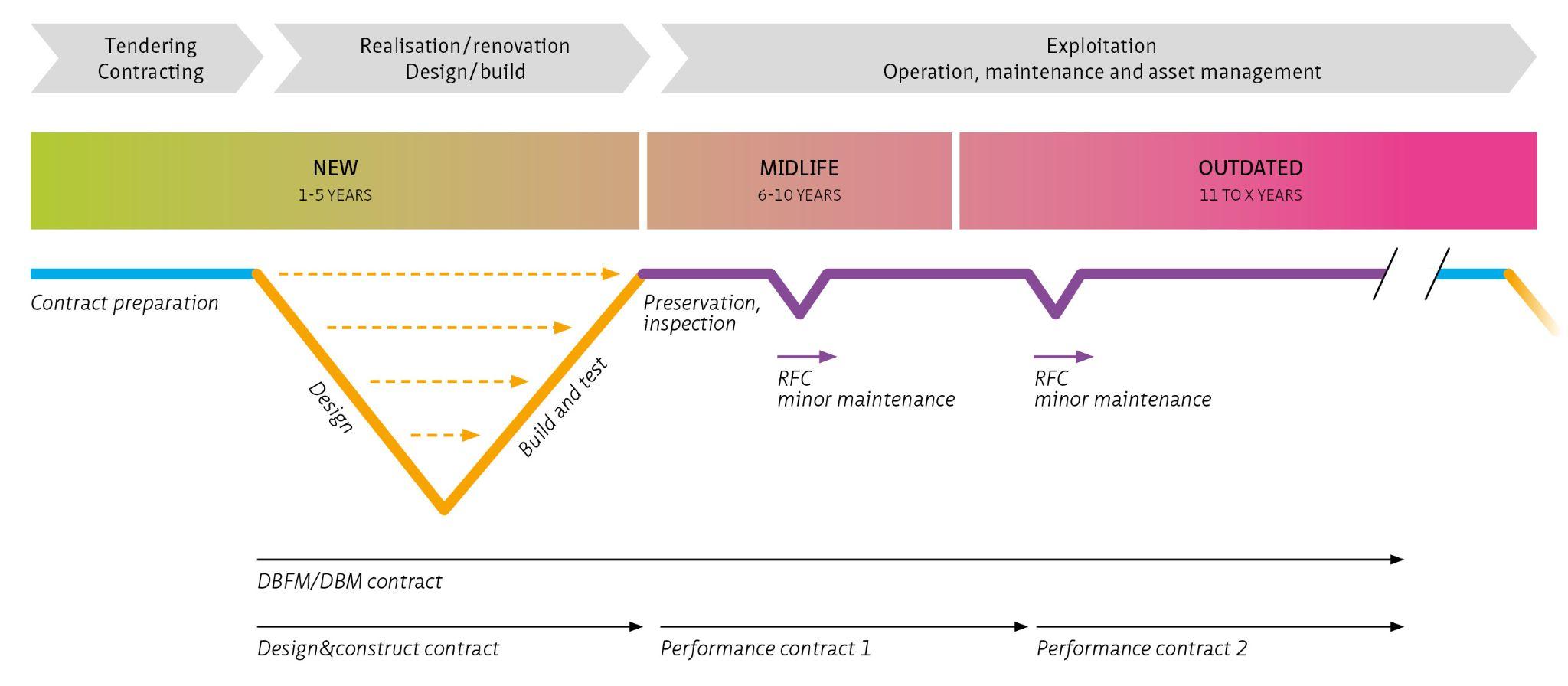
In the case of existing systems, the inventory is carried out on the basis of the current system design, the current measures and the current vulnerabilities (‘as is’). Following the risk analysis, new measures are introduced, effectively representing a new system design (‘to be’). In the event of new systems, the inventory is based on the intended operation and operational objectives, and the threats and designed cybersecurity measures.
Baseline measurement
On the basis of the list of risks, IEC 62443-3-2 makes it possible to make a baseline measurement and assess the threat risk without creating control measures. Using the baseline measurement, it then becomes apparent what the most significant risks are, and the control measures that are required to reduce the risk to an acceptable level. Precisely what that acceptable level is must be determined by the organisation that is going to manage the object to be created. They will be confronted with the consequences of the threat occurring, and the necessity of recovering normal functionality of the object within a reasonable time frame and at reasonable expense. Potential measures will be explored in the following section.
Project-associated risks
As explained above, there are also risks associated with the project itself. These are no longer those associated with the OT, but rather risks that are the consequence of the fact that the project generates information that is of potential interest to malicious third parties. This can then be subdivided into information on the project (who is working on it, how much it costs, how is the planning progressing etc.) and information on the object to be created (the design documentation). For the purposes of this living document the design documentation is particularly important: sufficient practical information relating to protecting information on the project can be found elsewhere.
If the design documentation falls into the wrong hands, there is a risk that a malicious third party could use it to investigate whether the design has any weak points, and how it is configured to counter threats. That is why it is important to carry out a risk analysis for this documentation, too. ISO 27005 can be used for this purpose. Subjects that must be addressed in this context are:
-
-
- Who has physical access to the design locations and the workstations on site? Access must be restricted to personnel who work there. There are measures in place to prevent access by unauthorised persons.
- Secure storage of the design documentation; who is allowed to do what, and how is this protected?
- What is expected of personnel working on the project in relation to communications, both internal and external, and how can design documentation be shared in a secure and reliable manner?
- How is the review and approval process set up, and what threats might it harbour? Who is allowed to see what, and how is this safeguarded?
- How are the computer systems that are used to create the design documentation protected?
Types of protection
When assessing actual access security, people look at security from the point of view of putting something tangible in place, such as a fence, lighting or guards. In this way it is possible to monitor and manage access to an object and its technical rooms and control cabinets.
Analyses in the context of technical security also have a bearing on the system hardware and software. This includes firewalls, antivirus scanners, secure links, the blocking of USB ports, encryption and mechanisms for identification and authentication. Control systems in tunnels use hardware that increasingly uses Internet technology to connect to a network. In relation to tunnels this is not just PCs and servers, but also cameras, network hardware, intercom, High-Frequency technology etc. It must be possible to use and service each device safely, remotely if necessary.
The security of technical measures is based on good faith in the products and their suppliers. After all, if there are backdoors or unpatched vulnerabilities in the product, this can totally undermine a security design. The products used must be configured and deployed safely, but they also need to be serviced long term (safety updates). Support offered by suppliers (of products) is crucial in this respect.
An important aspect of the analysis is to realise that updates not only remedy the errors; they often also introduce new or amended functionalities. It is important to test updates extensively before they are rolled out on the actual system. This may mean that a representative test/acceptance environment is required for each environment.